
Securing API keys prevents unauthorized access to sensitive resources and data. When API keys are not adequately protected, it opens the door to potential breaches and misuse. Unauthorized access can lead to data breaches, financial losses, and service abuse. Moreover, failing to secure keys can result in non-compliance with industry regulations, legal liabilities, and reputational damage. Securing API keys is a fundamental step in protecting both an organization’s assets and its reputation.
Securing API - Best Practices
Use HTTP/SSL:
A fundamental step in securing your API keys to use HTTPS and SSL for all your API interactions. HTTPS encrypts the data while it’s in transit, safeguarding it from interception and manipulation during transmission. SSL also authenticates the server’s identity, ensuring that you’re connecting to the genuine API provider, thwarting any potential malicious impostors. It’s imperative to never transmit your API keys and tokens over unsecured HTTP connections, as they become susceptible to capture by network sniffers or exploitation by man-in-the-middle attackers.
Store Keys securely:
Vital measure for safeguarding your API keys involve their secure storage on your server or device. Avoid embedding them directly into your source code, as this can lead to exposure through reverse engineering, debugging, or version control systems. Instead, opt for more secure storage solutions like environment variables, configuration files, or dedicated secure storage mechanisms like vaults, key stores, or secrets managers. These approaches enable you to encrypt, rotate, and invalidate your keys and tokens when necessary, as well as restrict their access solely to authorized users and applications.
Use scopes and roles:
Another important step in enhancing the security of your API keys is the utilization of scopes and roles to delineate and limit their permissions and access privileges. Scopes and roles enable you to precisely define the actions and resources that your keys and tokens are permitted to execute or access, along with specifying their duration of validity. For instance, you can employ scopes and roles to grant temporary read-only access to a specific endpoint or swiftly revoke access in the event of a compromised key or token. The adoption of scopes and roles not only helps mitigate the consequences of a security breach but also enforces the fundamental security principle of least privilege, ensuring that access is granted only as needed and no more.
Load into an environmental variable:
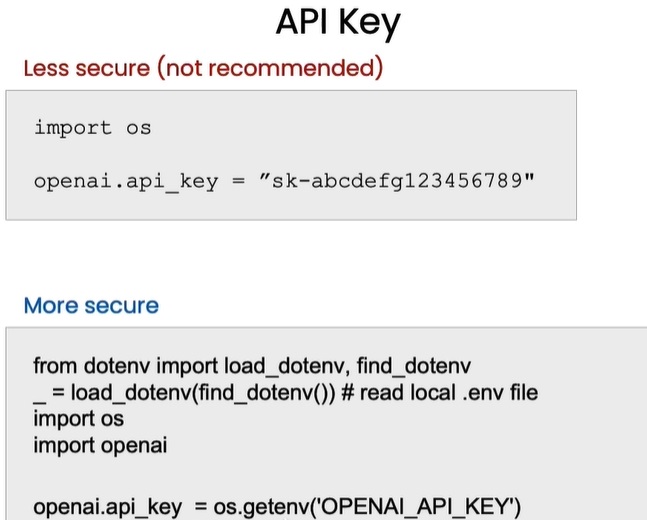
Many developers write the API key in plain text like this into their Python/Jupyter notebook and this is a less secure way of using API keys that I would not recommend because it’s just too easy to share this notebook with someone else or check this into GitHub or something and thus end up leaking your API key to someone else. In contrast, if you make a piece of code in python, where I use a library “dotenv”, and then run this command “load_dotenv”, “find_dotenv” to read a local file which is called “.env” that contains my secret key. And so with this code snippet, I have locally stored a file called “.env” that contains my API key and this loads it into the operating system environmental variable. And then “os.getenv, (‘OPENAI_API_KEY’)” stores it into this variable. And this whole process, I don’t ever have to enter the API key in plain text and unencrypted plain text into my Jupyter notebook. So this is a relatively more secure and better way to access the API key. This is a general method for storing different API keys from lots of different online services that you might want to use and call from your Python/Jupyter notebook.
Here is the code snippet:
Conclusion:
The secure handling of API keys is paramount in today’s digital landscape. These keys grant access to critical resources, data, and services, and their mishandling can lead to catastrophic consequences. Safeguarding API keys is not just a matter of protecting assets; it’s a commitment to upholding data privacy, maintaining integrity, and fortifying the overall security posture of an organization.
Posted by: Kamrun Analytics Inc.
Last update: December, 22, 2023
